We saved 10 million dollars of EOS from hackers!
EOS AuthorityMay 30th 2018The background
We at EOS Authority, are an EOS block producer candidate. Thousands of people visit our website every day to verify their EOS registration & find their account name. Running this verification system for the last 5 months also involves running a program to fetch all relevant information of the EOS ICO from the Ethereum blockchain.
We were running our final analysis on the registration database when discovered something odd in the data. That then lead to the message below
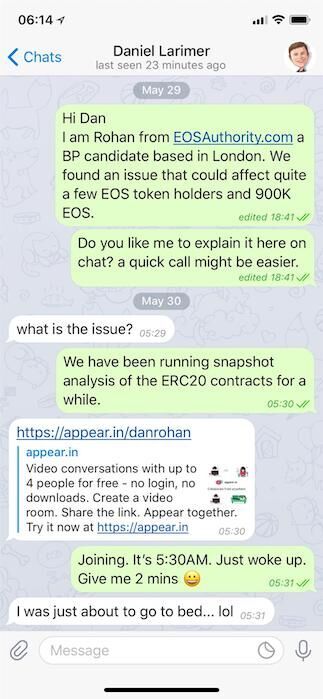
Alerting Dan and need emergency action !
The Issue
While running data analysis on the snapshot, we discovered that 213 wallets share the same EOS public key. This could have been one single user with so many different wallets. Very unusual, but still plausible given other weird things we've seen. After taking a closer look at the public key, it dawned on us that they've just used a publicly posted EOS public & private key pair. This means the public key used on 213 wallets was infact the same and the matching key was all over the web. The amounts in these wallets exceed $10 million at today's prices. With an average of about 3,866 EOS making it a total of 823K EOS.
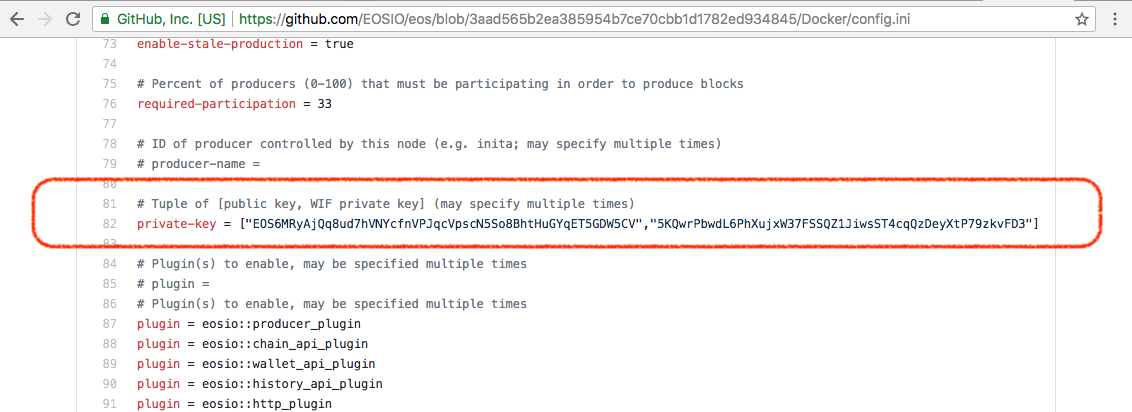
This public key was used to complete 213 registrations!
What an attacker could have done
The private key for all the wallets containing $10m worth of EOS is not private at all! As soon as EOS was launched, the funds could have been transferred out of the EOS mainnet. EOS has an amazing account security process, time delays and even an arbritation process. However none of these would apply here and the funds could have been taken off network.
Who is at fault here?
Clearly the people who used a EOS public and private key pair that they've just copied off from public sources and not generated themselves. For links on how to generate secure key pairs and learn more about registration, visit our registration campaign page.
How will this be fixed?
Those wallets affected will have to be immediately re-registered by the EOS holders. As an additional safeguarding measure, this morning, we've alerted the team at B1 and agreed upon a way to fix this issue. Sean Mitchell (a.k.a Sandw1ch) has fixed this issue on the snapshot process.
Does this affect me?
Are you a holder of one of the 213 wallets that have used this public key for your EOS registration?
EOS6MRyAjQq8ud7hVNYcfnVPJqcVpscN5So8BhtHuGYqET5GDW5CV
If yes, you need to act immediately and re-register. After you have completed this, drop us a note! If you have not done this, the safeguarding mechanism will take over and apply the fallback method invalidating your registration.
Timelines
29th May 19:20 UTC - Issue Identified by EOS Authority in London
29th May 19:41 UTC - Alerted Block.One Privately
30th May 04:29 UTC - EOS Authority team on call with Dan Larimer
30th May 11:55 UTC - On call with Sean Mitchell (sandw1ch - Block.one) and fix agreed
30th May 12:56 UTC - Patch applied (under an hour! - Amazing sandw1ch)
30th May 15:55 UTC - Fix confirmed and going public
Bug bounty
Please note that there is a new bug bounty program in place. Please get in contact with Block One team who will resolve the issue quickly. We encourage everyone to contribute where possible.
Continue this discussion on Reddit and also join EOS Authority on Telegram.
